Security in companies has recently taken on a new meaning. It no longer refers to the physical security of preventing intrusions in the company’s facilities. We also refer safety to the protection systems deployed to ensure the cybersecurity of the company’s data. An important fact to emphasize is that security is not limited to a set of technological tools within the company’s networks, but also covers the protection of servers, employee credentials, and anything that may pose a threat in case of corruption or infiltration of strangers.
With the increasing value of information in the virtual world, hackers have developed many methods to get hold of the data of all kinds of companies. Similarly, cybersecurity software developers have joined forces to create a whole range of tools and services to keep criminals away from users’ precious information. Among these new services and tools, one can find cloud functionalities, firewalls, VPNs, data backup and recovery systems, virtual machines, or modern honeypots with which everyone can put cyber attackers to the test.
What Is It?
Honeypots are traps that we set up for criminals who want to steal our data. They are located on computer networks that can be the target of hackers. This trap not only alerts users when an attack occurs but also collects all possible information about the ahttps://www.forbes.com/sites/larryhawes/2012/03/06/types-of-business-networks/#1cc91f2e6ebbttack, such as where it came from, what system was used, what software, what the objective was, etc.
This versatility of the honeypot allows, on the one hand, to reinforce the parts of the security network that we want to protect, and on the other hand, to take action against those who have tried to violate the security of our network, in case we have been able to track them down.
Benefits of Using a Honeypot
Its operation is fascinating, to say the least. Honeypots pretend to be real system components, their own networks that the assailant can enter. Once this happens, the user can see all the information of the assailant, from what they are doing to the sections they are trying to enter. Such features are ensured by the completely closed simulated system of the honeypot.
Thanks to this tool available on the Nakivo official website, users can discover new forms of attack that we had not foreseen, identifying vulnerabilities inherent to their networks. Such knowledge can also help users employ more effective security solutions, design more advanced protection strategies, and develop an action plan once a real threat gets through to the system.
Honeypot Types
There are two honeypot types currently available.
Production Honeypots
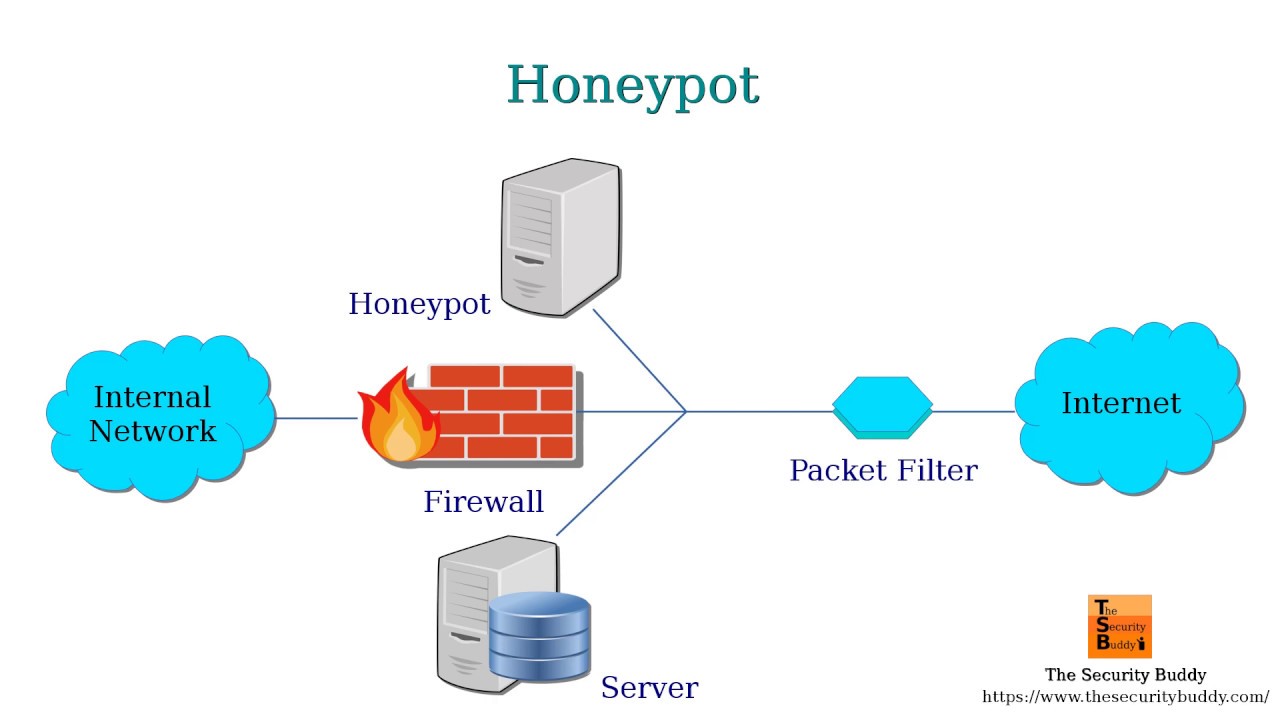
These are the systems that companies use to investigate why they receive cyberattacks from cybercriminals. The purpose is to find out why they have noticed that company and to try to divert or mitigate the risk of such attacks on your internal network.
Research Honeypots
They are used by non-profit organizations and educational institutions, where the only objective they pursue is to investigate the motives and ways that cybercriminals use to attack.
Should You Include Honeypots in Your Security Plan?
We can conclude that honeypots are one more ally in the fight for the security of networks. Along with other tools, they can detect intruders and correct anomalies that cause security breaches. The main virtue of the honeypot is the information it provides after its correct use, giving users a future advantage over another hacker, or even bringing to justice those who take the bait and fall into the trap.
Every day, companies allocate more and more resources to cybersecurity enhancements. Not only large multinationals and huge conglomerates but even small and medium-sized companies have found it necessary to cover their backs for keeping their businesses afloat. Thanks to tools like this, users can maintain a more secure network with an advanced shield, providing them with precious information about the attackers.
This tool, along with the basic ones mentioned above, such as backups, strong passwords, VPN, and a well-configured network, will ensure a promising and secure future in the business world.